Rotating Proxy Networks as Online Tools for Cybersecurity Audits
Expert cornerDiscover how rotating proxy networks enhance cybersecurity audits with anonymity, global reach, and uninterrupted monitoring.


Karolis Toleikis
Rotating proxy networks switch IPs to route traffic securely. This rotation hides identities and prevents easy detection. Proxy networks are vital for testing, monitoring, and vulnerability assessments. Auditors use them without exposing real IP addresses.
As audits rely on automation, rotating proxies boosts security. They keep operations consistent, private, and undetected online. Moreover, they enable auditors to gather threat data and simulate attack scenarios.
With the rapid evolution of cybersecurity, rotating proxy networks have become important online tools for yielding secure and data-driven audits. Let’s take a closer look at their key benefits, practical uses, and essential features to consider.
What Are Rotating Proxy Networks?
Rotating proxy networks automatically switch IP addresses for each request or session to mask the user’s identity and prevent traceability. Unlike static proxies that rely on fixed IPs, rotating proxies draw from large global pools, which offer dynamic and hard-to-block connections.
The rotating structure of these proxy networks enhances cybersecurity operations through anonymity, global accessibility, and uninterrupted monitoring. Here are some of the benefits of rotating proxy networks as online tools in cybersecurity audits:
- Anonymity and data protection
As mentioned, rotating proxies conceal user identities by constantly changing IPs. This approach prevents tracking, data interception, and network profiling attempts, strengthening overall data privacy across all audit activities.
- Global accessibility and IP diversity
Rotating proxies use worldwide IP pools to bypass geo-restrictions and local firewalls. This provides a secure way to access region-specific systems and data.
- Uninterrupted monitoring and threat detection
Rotating IPs prevents bans during vulnerability scans or OSINT collection. This way, monitoring is continuous and cyber defense tools are active.
Key Advantages of Using Rotating Proxy Networks in Cybersecurity Audits
A robust cyber defense helps protect sensitive data and keeps you ahead of threats. Organizations with employees who have taken up online cybersecurity programs can leverage rotating proxy networks to gain the agility and anonymity needed to find vulnerabilities before attackers do.
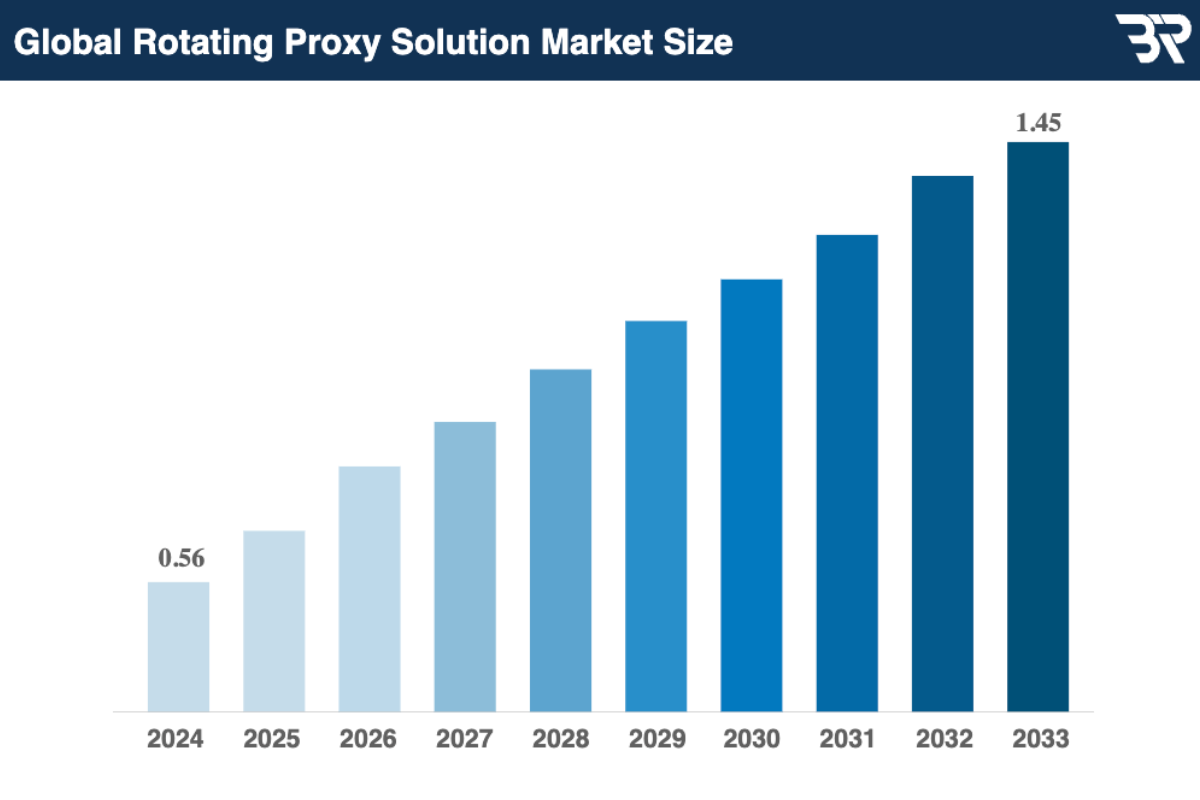
Moreover, the rotating proxy solution market , valued at $0.56 billion in 2024, is projected to increase to $0.62 billion in 2025 and reach $1.45 billion by 2033. This rapid expansion reflects the growing importance of proxies in modern security frameworks, as more organizations adopt them to enhance privacy, accuracy, and resilience in their cybersecurity audits.
Here are some more advantages of rotating proxy networks as online tools in cybersecurity audits:
Enhanced Anonymity
Rotating IPs hides auditor identities and prevents activity tracking during tests. Frequent IP changes remove traffic patterns that reveal testers. As a result, tracing actions to a single source becomes nearly impossible.
Effective incident response also relies on openness and transparency. High-resilience organizations promote accountability. According to the World Economic Forum report , 48% of them utilize anonymous reporting channels to facilitate safe incident disclosure and strengthen trust.
Accurate and Unbiased Data Collection
Proxies bypass IP blocks, ensuring complete and honest data access. They eliminate bias caused by rate limits or geo-restrictions.
As such, auditors can gather authentic insights from web applications or APIs across regions. This will result in analytics that reflect real-world conditions without distortion from throttling, censorship, or localized filtering systems.
Global Threat Visibility
Auditors test systems from worldwide IPs to detect regional threats. This expands visibility across varied attack surfaces and compliance zones.
By simulating global traffic, teams uncover region-specific vulnerabilities that standard scans may miss. This strengthens defenses against regional attacks and ensures global compliance.
Continuous Monitoring
Automatic IP rotation maintains uninterrupted scanning and analysis. It supports ongoing vulnerability detection within CI/CD workflows.
Each rotation prevents IP blacklisting during continuous assessments for seamless and long-term monitoring. As a result, teams get real-time security insights to patch vulnerabilities promptly.
Secure Communication Channels
Encrypted proxy connections protect sensitive audit data in transit. They isolate internal systems and maintain secure communication layers.
Proxies create an additional layer of protection between internal networks and external endpoints, minimizing exposure risks. This architecture safeguards credentials, configurations, and test outputs from interception and tampering.
How to Integrate Rotating Proxy Networks Into Cybersecurity Audits
Integrating rotating proxy networks into cybersecurity audits is easier said than done. The process requires strategy, compliance, and technical precision. You need a proper setup to align with organizational security goals and international data protection standards such as GDPR, HIPAA, and ISO 27001.
In the United States, legacy infrastructure remains a major cybersecurity challenge ; 52% of states cite it as a barrier to addressing threats, while 59% struggle to support emerging risks. Rotating proxy networks help overcome these limitations by introducing flexible, scalable, and modern audit capabilities.
The idea is to build integration around your existing cybersecurity framework. From assessing proxy compatibility with scanners to optimizing rotation logic and training staff, every step plays a role in improving audit depth and resilience.
Ensure that you configure your rotating proxies correctly to enhance audit accuracy, protect sensitive data, and improve visibility across distributed systems. Below are practical steps to ensure the seamless and secure implementation of rotating proxy networks as online tools.
Audit Current Online Security Tools and Data Workflows
Review existing scanners and workflows for proxy compatibility. Use tools like Tenable Nessus, Qualys, or OpenVAS. These tools integrate well with proxy-based routing and enhance vulnerability detection and OSINT operations.
You should also determine where rotating proxies can provide additional coverage or ensure safer data collection.
Select Reliable Proxy Providers
Choose proxy providers with strong uptime, a diverse IP pool, and transparent privacy policies. It also helps to focus on vendors that offer residential and mobile IPs, SSL encryption, and flexible rotation intervals.
Make sure to test for speed, reliability, and data accuracy before full deployment to ensure consistent audit results.
Configure Rotation Logic
Set rotation per request for broad vulnerability scans and per session for focused penetration tests. Apply geo-targeting to simulate attacks from specific regions or verify compliance with data localization laws.
With proper configuration, your cybersecurity audits remain efficient, undetected, and contextually accurate.
Train Security Teams
Educate IT and SOC personnel on proxy configurations, ethical use, and interpreting proxy-based audit data. Invest in proper training to reduce configuration errors and strengthen the effectiveness of continuous monitoring and automated scans.
You may also include regular refresher sessions to maintain best practices.
Monitor and Optimize
Use monitoring tools such as Zabbix, Prometheus, or Elastic Stack to track latency, connection success rates, and block frequencies. After which, make it a practice to regularly evaluate rotation performance and fine-tune provider settings to maintain efficiency.
The habit of continuous optimization ensures your rotating proxy network stays reliable across all audit phases.
Strengthen Cybersecurity Audits With Smart Proxy Management
Smart proxy management empowers organizations to conduct safer and more accurate security audits. By rotating IPs, proxies conceal real identities and reduce detection risks. As a result, teams can gather reliable data and test systems securely. Moreover, configuring rotation logic boosts efficiency and prevents unexpected audit disruptions.
Invest in proper training for your security teams to interpret results faster and patch vulnerabilities promptly. This way, you can maximize the use of continuous online monitoring tools to track latency and identify potential blocks early.
We recommend you choose reliable providers with strong uptime, diverse IPs, and encryption. Remember, the right choice of tools reveals regional weaknesses and compliance gaps. Stay strategic with your proxy management to turn audits into proactive defenses.