Data Security Best Practices to Safeguard Your Business
News

Justas Palekas
The importance of data in the current commercial landscape cannot be overstated. From retail to entertainment to healthcare, each sector relies on massive amounts of information to make more accurate predictions. Forbes outlines that data-driven enterprises have a significant competitive advantage and will likely outlive the competition that relies more on intuition than verifiable facts.
Using online data safely and according to the law requires several considerations. We have already covered the ethical considerations in data collection so that you don’t become the next Cambridge Analytica or avoid issues that plague Google’s Incognito mode. This time, we will review the data security best practices that you can implement to protect your data and ensure compliance with the law.
With adequate employee training and cybersecurity software, you can avoid losing expensive information sets or, even worse, leaking confidential client information to cybercriminals. The recent Cost of a Data Breach Report 2023 , carried out by Ponemon Institute with IMB oversight, analyzed 550 organizations hit with data breaches. It revealed that the average data breach cost globally was $4.45 million , which is 15% more than three years ago.
What’s more, data protection regulations like GDPR oblige businesses to protect data, and failing to do so can have lawful consequences. To help you avoid these risks, here are data security best practices to prevent data breaches and data theft.
What Is Data Security?
Data security is a process of protecting digital information from theft, unauthorized access, and malicious modification. It is an ongoing process that oversees information gathering, storage, and transfer..
To be concise, we can refer to the three-letter acronym CIA.
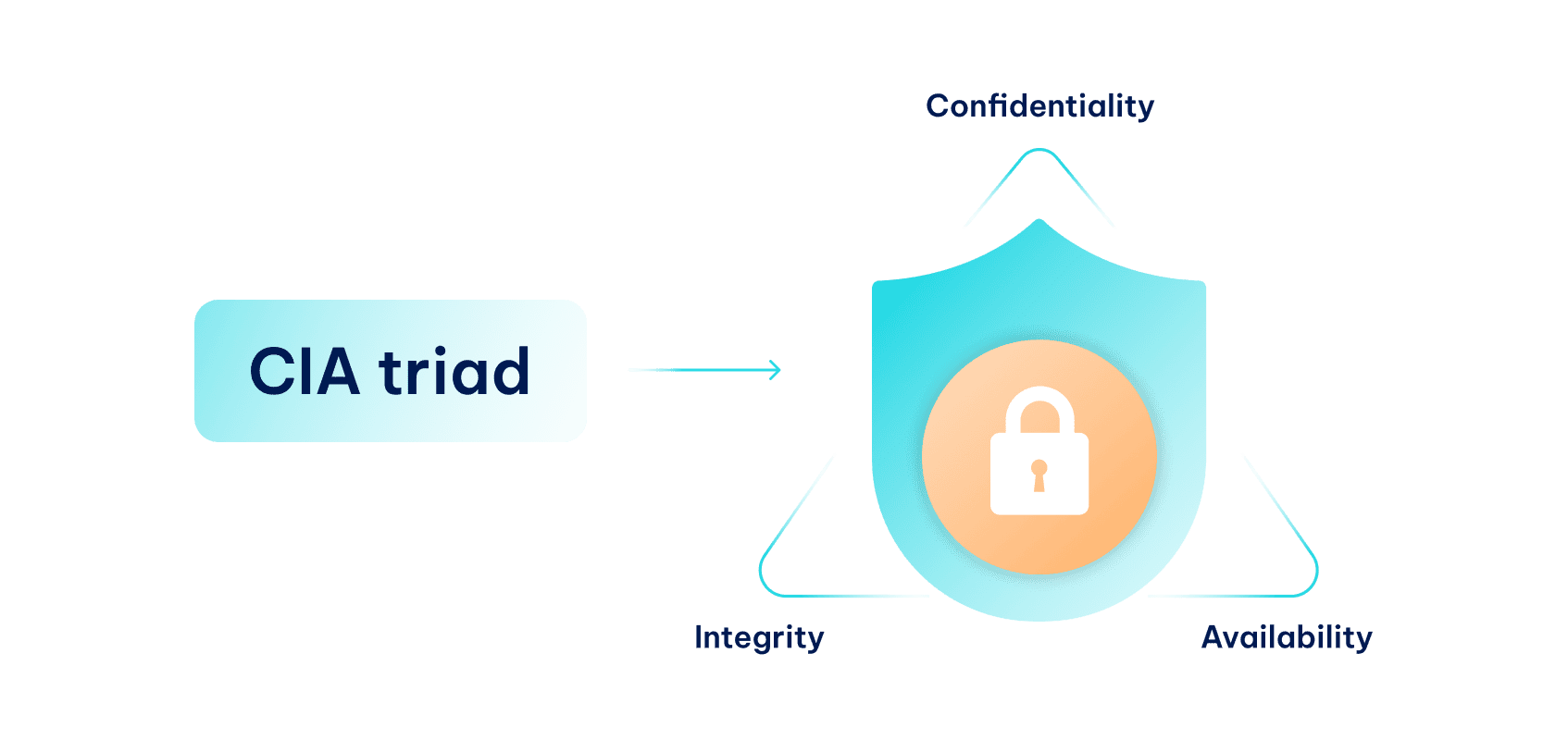
- Confidentiality: protecting data access from unauthorized parties.
- Integrity: protecting data from unauthorized modifications, corruption, and deletion.
- Availability: maintaining uninterrupted data access to authorized parties.
To achieve CIA, we will outline technical decisions , like network segmentation; software solutions , like data encryption and password managers; but also non-technical aspects , like employee training, adherence to national and global data protection laws, and workplace rules.
Understanding that data security best practices are a multi-part ongoing process is paramount. Your business must quickly respond whenever cybercriminals breach the workplace network to steal confidential information.
Simultaneously, you must also notify authorities in a timely manner if your systems have been breached. After the 2014 Yahoo hack, the Securities and Exchange Commission fined it 35 million dollars because the company did not disclose the incident until 2016.
As you can see, adhering to the data security best practices helps you avoid unnecessary financial losses. Let’s start with data categorization.
Identify and Classify Your Data
Not all data is equally important. Some of it is only for one-time use, like exclusive holiday discounts that disappear after the sales. Afterward, it becomes useless, and leaking or deleting it will only damage your business if you have specific future plans for it. However, sensitive information like client’s confidential data, personally identifiable information (PII), research and development sensitive data , and alike requires continuous safeguarding.
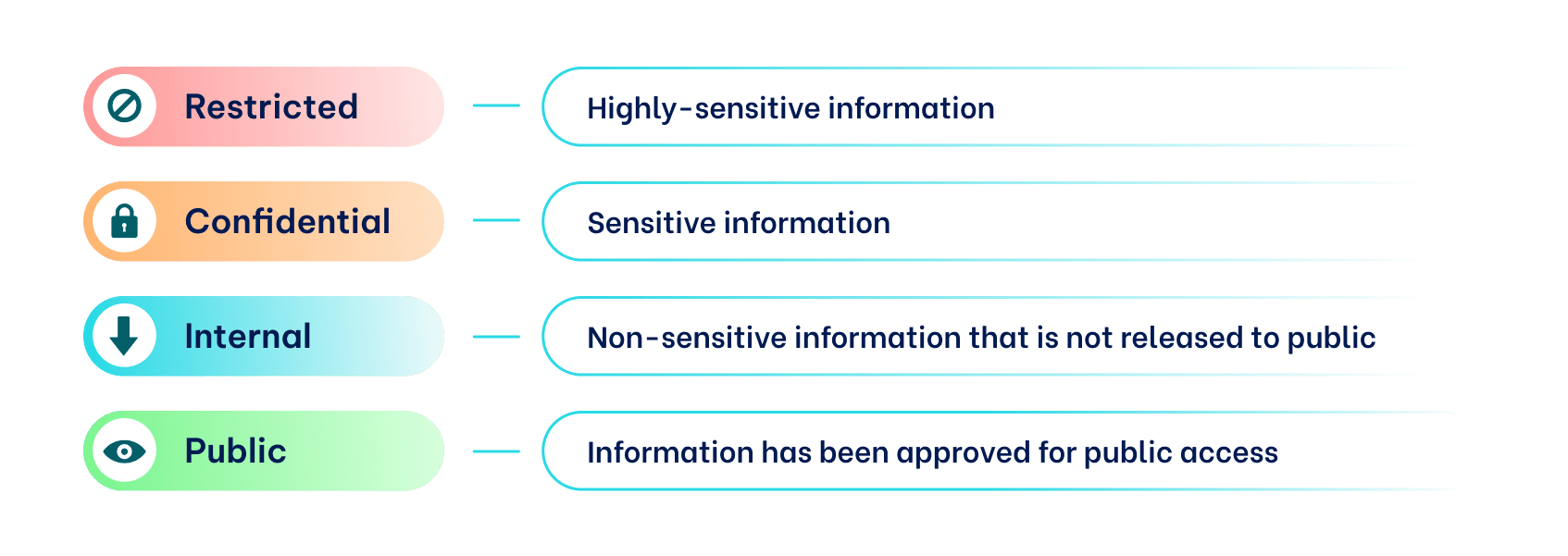
To make things easier, separate data that is widely accessible and does not violate any data security and privacy laws from critical data that unauthorized parties cannot view. We recommend using these four categories:
- Public data
Information that can be shared freely with anybody without any lawful repercussion.
- Private data
Data that can be accessed by employees and authorized third parties, but is not available for public view.
- Restricted data
Data that is protected by the law and cannot be shared with anyone except by a lawful recipient, like financial or medical information.
- Confidential data
Highly secretive data that is not necessarily protected by specific laws but is available only to a small selection of viewers, like business secrets.
Data classification into these categories lets you implement adequate access controls and separate sensitive data from public view. This is highly beneficial if your business deals with a lot of information because some of it requires restricted access controls protected by multi-factor authentication, encryption, and data backups. Meanwhile, you can save network resources storing publicly available and non-essential data without spending extra on expensive cybersecurity procedures.
Another significant benefit is risk assessment and risk management. Your system’s administrator can raise the on-the-spot alarm if they notice unauthorized access to sensitive data. That would be much harder to identify if the data was not separated and was stored with the same access controls. Furthermore, it is immediately apparent which data segment was breached, and if it’s restricted or confidential information, then the threat level demands instant attention.
Implement Strong Access Controls
Implementing strong access controls is one of the first steps to securing sensitive data. It is a crucial responsibility for all businesses that deal with client data. Failing to protect sensitive information not only results in significant reputational damage but also undermines the trust users have in the company’s ability to safeguard their privacy.
In 2019, Facebook was caught storing up to 600 million user account passwords in plain text that were available to thousands of their employees. This time, Facebook avoided legal fines due to the lack of evidence of password misuse. However, after confirmation, its shares shrank by 1 percent, further worsening the enterprise’s public perception.
Imagine if Facebook had insider threats that could access up to 600 million user accounts due to this serious security vulnerability. It took 80 million profiles to cause the Cambridge Analytica scandal, one of the last decade’s most significant online privacy violations. Furthermore, people share a lot of intimate details over the platform (address, telephone number, pictures, etc), which makes data security even more critical.
Considering the risky consequences of a security breach, following the Principle of Least Privilege (PoLP) is not just a good practice; it’s a necessity. This principle ensures that each employee has the minimum level of access necessary only to perform their task, reducing the chances of unauthorized access by rogue employees.
Principle of Least Privilege
This principle controls who has access to what information that’s required for their tasks. The logic is that an employee should have access only to information that is necessary to fulfill a specific piece of work, but not more. This significantly reduces the chances of insider threats accessing sensitive data but requires additional software to set up access privileges, which can be done, for example, with a business password manager.
Afterwards, a regular review is essential. Employees should be stripped of access privileges once they are done with their assignments. If your business uses passwords for data security, they should be changed in case an employee copies them. Furthermore, contemporary data security software allows asking for and granting access privileges with a few clicks and an organized dashboard for oversight.
User Account Management
For decades, passwords have been the primary method of protecting digital accounts. Although they are still the most common user authentication method, the days when you could use ‘password123’ or ‘qwerty’ safely are long gone.
To put things into perspective, consider the Colonial Pipeline hack. Attackers compromised a weak password used to ‘protect’ a VPN account. After hijacking the VPN account, they could connect to the company’s internal network as an authentic user. The attackers infected the network with ransomware, halting the largest refined oil pipeline operations in the US and causing millions in damage.
Currently, some enterprises are shifting away from passwords to fingerprint, facial, iris, or voice recognition. Alternatively, some use physical security tokens (like USB security keys). Each of the alternatives has strong points and vulnerabilities, so the passwords are as relevant as they have ever been. However, with the rapid evolution of cybersecurity software, it is now possible to combine a few methods, like a strong password with a multi-factor authentication (MFA) or a Single Sign-On (SSO) technology.
A reliable business password manager is an excellent data security tool. Firstly, it allows storing as many long and complex passwords as required. This cybersecurity software offers password auto-filling, which means it copies and pastes the password automatically without employees typing it.
This way, employees don’t have to remember passwords by heart or type a 60-symbol string, so they feel much more comfortable using secure passwords. It also neutralizes spyware that takes screenshots to capture and steal credentials.
Business password managers allow system administrators to set up and control hundreds of accounts simultaneously. They can clearly see which employee is accessing what account, adhering to data security guidelines. Administrators always know who has access to sensitive data and can revoke the privileges that look like data breaches.
Multi-Factor Authentication
MFA is one of the data security best practices that protect sensitive information when other defense lines fail. Without it, cybercriminals could immediately access an account if they guess, steal, or hack the password. Instead, MFA ensures an additional verification activates whenever unrecognized devices attempt to access accounts , even if it uses a correct username and password combination. MFA can also trigger on each login attempt, which is highly recommended for the most important data protection.
When it comes to multi-factor authentication methods, there’s no one-size-fits-all solution. The choice of verification method should be carefully considered, tailored to your specific data protection requirements. Here are some of the most popular options to guide your decision-making process.
Security Question
One MFA method involves the use of a personal security question for additional verification. After entering the username-password combination, an employee will be prompted with a security question. This could be anything from ‘Which school did you go to?’ to ‘The name of your first pet,’ or ‘What’s your favorite music band?’.
However, it’s important to note that many security questions can be guessed based on information found on social media or search engines, making this the least secure MFA option.
One-Time Passwords (OTPs)
After a successful login attempt, the employee will be asked to input a second password. It could be sent via SMS message or email. Even if hackers obtain the correct account credentials, they do not have access to a secondary device or account that receives the OTP.
Although this MFA option is susceptible to SIM swapping , hacking a smartphone or an email is significantly more complex than brute-forcing credentials.
Mobile Authenticators
Mobile authenticators are among the most popular MFA options. A secure third-party authenticator app is linked to a selected account. Whenever an employee accesses a named account with a password, they must confirm it using an authenticator app. To hack an account, an attacker must have access to an employee’s smartphone, which repels most attackers.
Data Encryption
You cannot list data security best practices without data encryption. The internet in its current state would not be possible without it, as all chats, banking transactions, and other types of data exchange would be visible to everybody. Encryption scrambles data, making it undecipherable to unauthorized parties but viewable to legitimate recipients.
You must encrypt all client data if your business collects and stores personal information. For example, Windows offers a BitLocker that encrypts the entire drive. If your employee device has a password enabled, even if someone steals it, they cannot decipher encrypted data. However, it’s best to rely on professional third-party data-at-rest encryption services that provide broader customization options and secure data sharing to prevent data breaches.
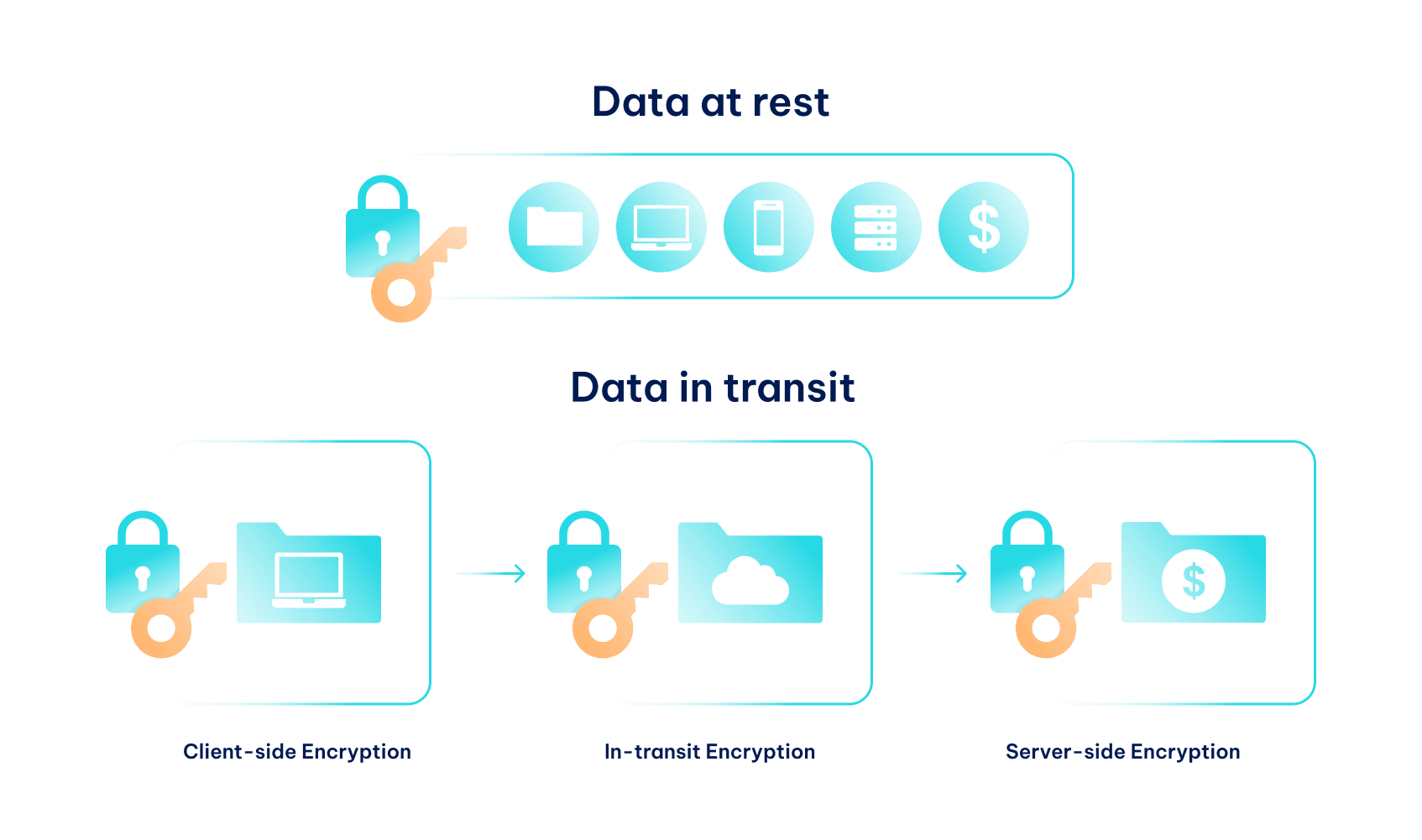
Simultaneously, you must ensure data-in-transit encryption. Although the majority of online communication happens over secure HTTPS protocol that encrypts traffic by default, it is highly advisable to use a VPN whenever your employees connect to your workplace network remotely. A VPN uses additional encryption algorithms to safeguard sensitive data from undesired attention, significantly contributing to data security.
Secure Your Devices and Network
Having covered data classification and protection from unauthorized access, the next crucial step is to understand the role of endpoint security systems in achieving comprehensive network safety.
Antivirus and Antimalware Software
Often used interchangeably, it’s best to make sure your chosen cybersecurity software protects from viruses and other types of malware simultaneously. Viruses are malicious programs that replicate and spread throughout a network , infecting chosen targets. A good antivirus offers real-time security incident detection and alerts that it has detected a threat. It will quarantine the threat, which you can inspect and remove on demand.
Malware is a broader concept that includes trojans, spyware, works, and extremely dangerous ransomware. A sophisticated cybersecurity tool has a more elaborate inspection spectrum and can identify numerous different types of malware. Such software is paramount for all businesses, as cybercriminals attack small or big ones without differentiating, especially if they lack sufficient data security protocols.
Firewall
Similarly to an antivirus, a firewall is essential to data protection, and data security best practices must deploy both. These two are similar in that they protect digital systems from threats.
However, the firewall is oriented toward network security, while antivirus protects individual devices. Imagine a firewall as a guard at your company’s gates. It inspects incoming traffic for malicious elements, called network filtering , and neutralizes the threats before they can cause damage.
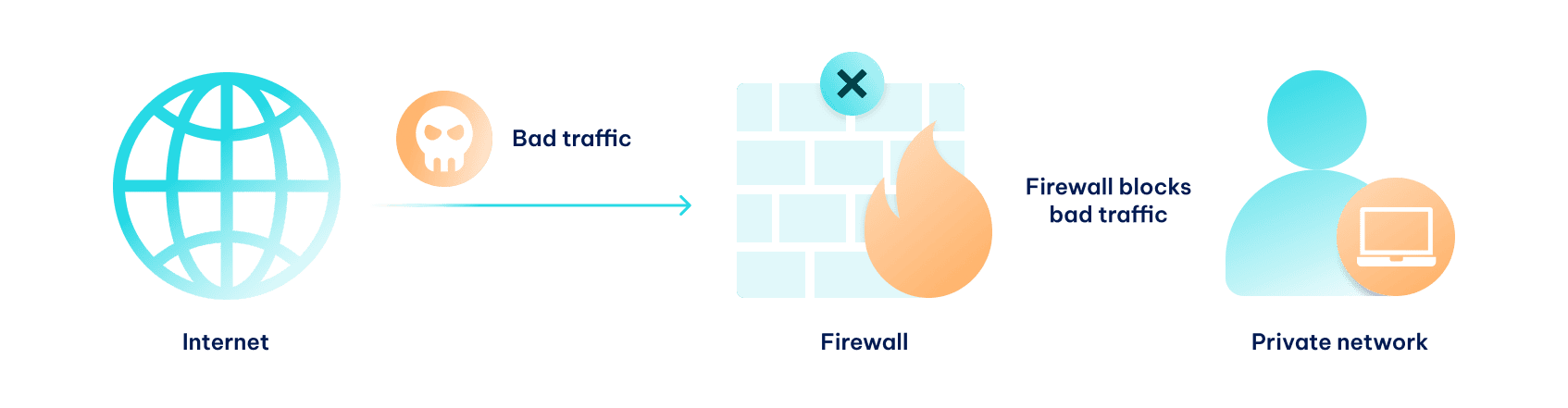
It’s worth noting that proxy servers can also be used for network filtering. Primarily, it works on the URL level, setting up rules to prohibit access to selected websites. SOCKS5 proxies also support user authentication, asking for a password before providing access to the internet and expanding network management options.
Physical Security
Because we’re discussing digital data, the physical security side is often overlooked. Nevertheless, it is just as crucial for data protection. Firstly, it is paramount to secure physical access to servers with employee badges and/or biometric authentication. Providing access to server rooms for anybody is calling for a data breach to happen.
It would be best if you also considered server room temperature, fire suppression and alarm, and humidity. Servers heat up, resulting in a damp environment, which will cause physical damage, downtime, and even data loss if left unattended. Lastly, avoid locations with frequent natural disasters, as losing your servers to a flood or a tornado is devastating if you have not backed them up.
Employee Education and Awareness
According to Verizon’s 2023 Data Breach Investigations Report , 74% of data breaches were caused by human error. This shouldn’t surprise you, as hacking expensive cybersecurity software is much harder than social engineering or tricking people into sharing passwords via phishing. The rapid development of AI technologies also allows for the crafting of deepfakes and the translation of scams into other languages to personalize them.
Employee cybersecurity awareness training will significantly improve workplace safety. What’s more, it can positively affect productivity and comfort, as workers no longer have to worry about external online threats. Comprehensive data security training should include the following:
- Basic cybersecurity concepts (threat, vulnerability, malware, etc.);
- Data categorization;
- Phishing and social engineering identification;
- Safe password management;
- Different malware types, their features, and identification;
- Reporting security incidents;
- Work device security;
- Cybersecurity software training.
The list can be complemented with business-specific topics, like cloud system security, sensitive data handling, smartphone malware, etc. The data security best practices schedule regular cybersecurity training because employees must be updated on the latest cyber threats and the most efficient data security practices.
Regular Backups and Disaster Recovery
A regular data backup is one of the most important parts of data loss prevention. As much as we don’t like the hard truth, a perfect data security system does not exist. Most businesses will encounter an accident sooner or later (hardware failure, natural disaster, deletion by mistake, malware attack), and the best way to mitigate damages is to be prepared.
We recommend considering the 3-2-1 backup rule. It advises having three copies on two different media (USB drive, cloud server, NAS, etc.), with one copy stored offsite. This way, if one backup fails, you can always turn to another one. If both on-site backups fail, you can retrieve the offsite one to restore sensitive data and continue working. Pay close attention to the fact that the offsite copy must be disconnected from the workplace network to avoid risks like ransomware contamination.
Keep Your Software Up-to-Date
To keep your workplace network and devices safe, you should never postpone system and software updates. After discovering a vulnerability, cybersecurity developers hasten to patch it up. They release a vulnerability hotfix and release it to all users. Those who fail to apply the update on time leave their devices open to exploitation.
All employees must be directed to apply updates to their work devices immediately. Furthermore, if they install any software unrelated to their tasks, it must also run on the latest version. Keep in mind that cybercriminals use tools like a Shodan search engine that can reveal a software version. Hackers then search for online devices that run unpatched software with known vulnerabilities and attack them.
Last Words
These are the essentials of data security best practices. Contrary to some beliefs, cybersecurity cannot be achieved in one giant step. There is no magical software that will ensure comprehensive data security. Instead, it is a combination of different processes administered by professionals.
Any large enterprise should avoid trusting all security aspects with one employee. A system administrator might not be familiar with the latest malware threats known to malware analysts, and information security specialists may not be familiar with cybersecurity software deployment.
To summarize, we recommend classifying your data, ensuring secure access controls following the principle of least privilege, using strong passwords and MFA, encrypting data at rest and in transit, and having a reliable antivirus and firewall. Furthermore, you should have regular backups, employee training, and timely system and software updates. Although each business has specific data security requirements, these data security best practices will apply to most.
