There are several online privacy protection tools, like proxies, VPNs, anti-detect browsers, and browser fingerprint spoofers. One service stands out among the rest, although as a combination, but not a replacement. That’s the Tor (the onion router) network and Tor browser.
Currently, this online anonymity tool is used by over 7 million people worldwide. However, there is no such thing as complete online anonymity, so it is best to familiarize yourself with Tor’s limits and capabilities and how proxies can strengthen its weak points.
What Is Tor Network?
Tor is a network of relays accessible through the Tor browser and designed to anonymize users’ online activities to a specific and high-level point. A Tor relay is similar to a proxy server, but it also encrypts traffic, resembling a VPN. However, that’s where similarities end because Tor uses unique multi-layered encryption, nearly 8,000 volunteers run its relays, it is open-source software, and it hosts servers only available through Tor browser, called onion services.
One of the most significant differences is that Tor uses the onion routing protocol. This protocol works by sending user traffic through multiple relays, also called nodes. The first (entry) node encapsulates data, applies multi-layered encryption, and sends it to a middle node, which forwards it to an exit and final node. Usually, the traffic bounces from 3 to 6 relays. This forms the whole of the Tor network. The final node sends encrypted data to the target destination, exiting the Tor network.
Although such a data transfer structure remarkably protects users’ online activities from surveillance, it has its shortcomings. One of the biggest setbacks is that the entry node knows the user’s original IP address. A malicious actor can pose as an entry node and, by knowing the original IP address, identify the user and track them online. This brings us to proxies and how they contribute to strengthening online privacy protection over Tor.
Why Use Proxies With Tor?
A proxy server enhances Tor in a few meaningful ways. Firstly, authoritarian countries like China, Russia, and Iran restrict access to Tor download sites. In this case, a user can connect to a proxy server in a country without such restrictions. We recommend residential proxies to bypass geographical blocks because they are the best at mimicking a genuine user from a different location.
A proxy server also solves the entry node’s potential vulnerability. Because the user connects to a proxy first, which takes over online communication and assigns a new IP address, the entry relay sees only the proxy IP without obtaining the original one. It protects against numerous IP-based cyberattacks, like DDoS, and surveillance via IP tracking simultaneously.
In some cases, a proxy server placed closer to a target destination server can increase the connection speed. Although rarely, you can experiment with this method if you encounter significant lag and know the target server’s geographical location. This time, you can try datacenter proxies first, as they generally offer the best uptime and connection speed.
Which Proxy Is Best for Tor?
It is highly advisable to use residential proxies for Tor. They are designed to mimic a genuine user and, unlike datacenter proxies, excel at online privacy protection. Simultaneously, residential proxies are best for overcoming geographical restrictions to access the Tor download site in countries where it is blocked.
However, if you experience significant connection speed or latency issues mentioned in the paragraph above, you can experiment with datacenter proxies. Choose one closer to the target server and double-check the results with a speed test. Although Tor slows down traffic due to multiple hops, this solution can help minimize the issue.
How to Set Up a Proxy in the Tor Browser?
For visual learners, watch this video:
While the structure of the Tor network sounds complex, it’s because it is. Tor is a highly sophisticated online privacy protection tool. However, using it is particularly easy, and the same applies to Tor proxies.
1. Go to the official Tor website and download it.
2. After installing it, launch the browser, and on the opened window, choose the Configure Connection option.
3. Then, scroll down through the numerous customization options to the very bottom. You will see the Advanced section, where you have to click on the Settings button.
4. As you can see, these proxy settings are reserved solely for the initial proxy connection so that you can set up a proxy directly in the Tor network settings. As an example, I will use IPRoyal’s HTTPS residential proxy servers. Configure your proxies in the IPRoyal dashboard.
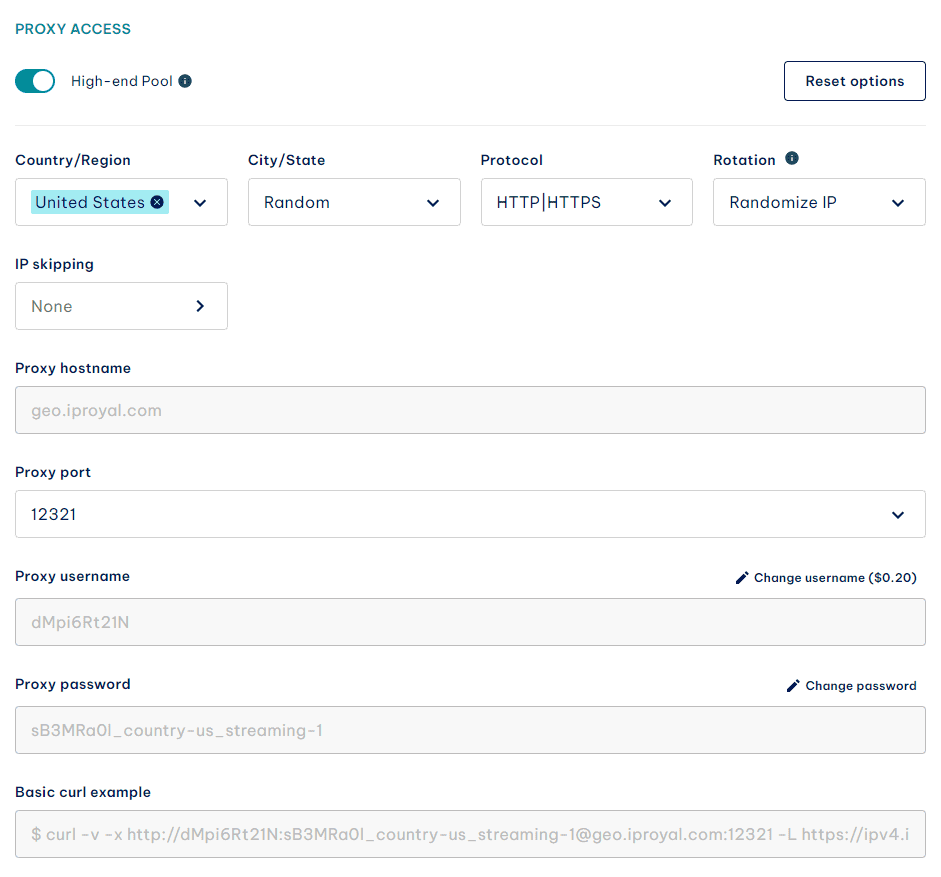
5. Get your proxy details (hostname, port, username, and password) and add them to Tor. Click OK when done.
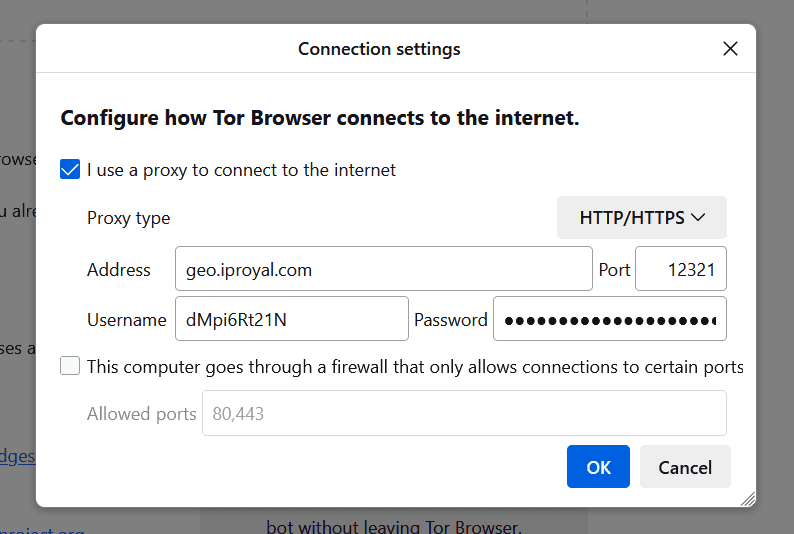
6. Close the Settings tab and go back to the main window. This time, click the Connect option.
7. It will take up to a minute to connect to Tor.
8. Now, you can browse online with highly strengthened privacy protection, suitable for political activists, journalists, and victims of violence seeking anonymous assistance online.
9. To verify that it works, I have checked my IP address details on ipleak.net. Here are the results.
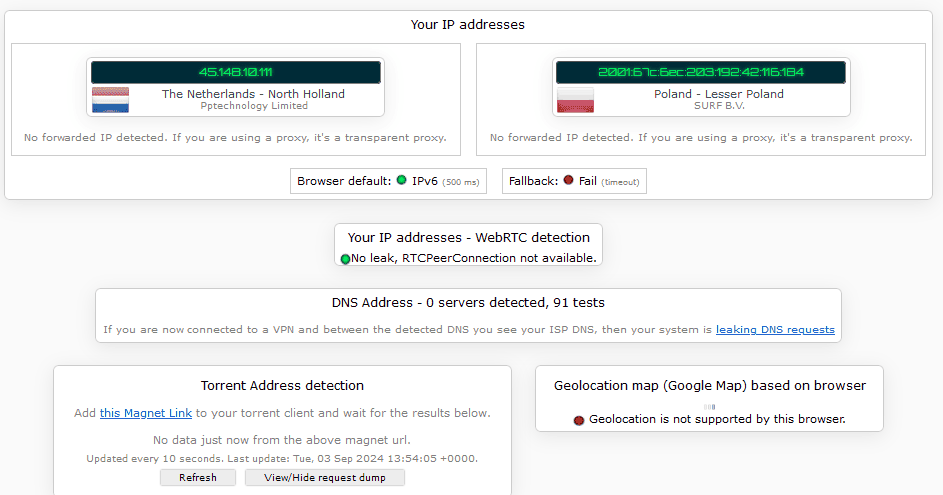
None of the IP addresses are mine, so the proxy and Tor combination successfully obfuscated my information. There are no DNS leaks, so the browser is using proxy DNS instead, and the geolocation tracking is disabled, which is expected from robust privacy protection tools such as Tor.
Conclusion
Tor is remarkable in its ability to cloak online activities from surveillance. However, there is no such thing as 100% online anonymity. It is an ongoing process that requires multiple tools. Proxies are one of them, and they help secure Tor’s entry point and hide your original IP address from all relays. This way, your device remains safe even if any node is compromised.



