Zero Trust Security Framework: How it Works And Best Practices
Expert corner
We live in a world of ever-increasing complexity and sophistication. Technology is constantly becoming quicker, more responsive, and more intelligent. While this offers opportunities, any business that works online - with the rise of software such as cloud-based contact center solutions which includes most companies - has to be aware of the accompanying risks.
Cloud-based data environments and an increased number of workers logging in from unsecured laptops at home mean that traditional security strategies are looking outdated. Because your network is accessible from more and more places, new vulnerabilities become clear.
The first half of 2022 saw 2.8 billion malware attacks - an increase on 2021 - while more complex attacks are also growing.
Rather than assuming that internal users of a network are safe, modern security frameworks need to accommodate these new risks. Zero Trust security is the best way to counter these new challenges.
What Is Zero Trust Security?
So, what is a Zero Trust security framework? The clue is in the name: this is an approach to business proxy server that begins with an assumption that every activity in a network is a threat. Traditional network security solutions would trust a network’s users once they had verified access in the beginning. In practice, this would look like logging into a network once on a laptop and no longer having to log in again.
However, Zero Trust recognizes that network users can now become compromised once they have access within a security perimeter. In short, it has ‘Zero Trust’ in both external and internal activity.
Coined by John Kindervag - an analyst at Forrester Research - in 2010, the concept of Zero Trust security has since been used across a wide range of businesses and companies. Google was one of the first major online companies to implement this approach to online security. Any online business with enterprise-grade IT should look to use a Zero Trust framework.

How Does it Work?
The main principle of Zero Trust security - to “never trust, always verify” - requires certain specific features to work. As 34% of security breaches involve internal actors, constant verification is a crucial aspect of Zero Trust. Rather than just allowing users to verify once, Zero Trust works by ensuring that multi-factor authentication is used every time a user wants to access the network.
Multi-factor authentication is already being adopted across the internet. Many AWS application modernization processes will now include multi-factor authentication. However, it isn’t enough to allow users access to the entire network once they have verified. After all, Zero Trust assumes that all internal activity in the network is a potential threat. Zero Trust, therefore, uses the principle of least-privilege access.
It requires that once users have verified using multi-factor authentication, they are then able to access only the specific parts of the network that they need to. It means that network users are securely verified whenever they require access to new parts of the network and that their verification doesn’t open up access to all of the network with potentially sensitive data and information.
Multi-factor authentication reduces the risk of successful cyberattacks, but some may still enter your network. Least-privilege access means that any cyber threats that do manage to exploit the necessary access points to your network can’t reach all of your data.
As well as continuous verification and least-privilege access, Zero Trust security also works by considering encryption through the framework of Zero Trust. Sensitive information and data - such as passwords, customer information, or internal communication - should be encrypted and accessible only to a limited number of network users.
With more big companies using online systems - for instance, hosted VoIP phone systems - data that is stored in the cloud needs to be encrypted securely. Many companies will need to use such strict encryption of customer data to comply with regulations such as GDPR , but it is also an integral part of how Zero Trust security works.
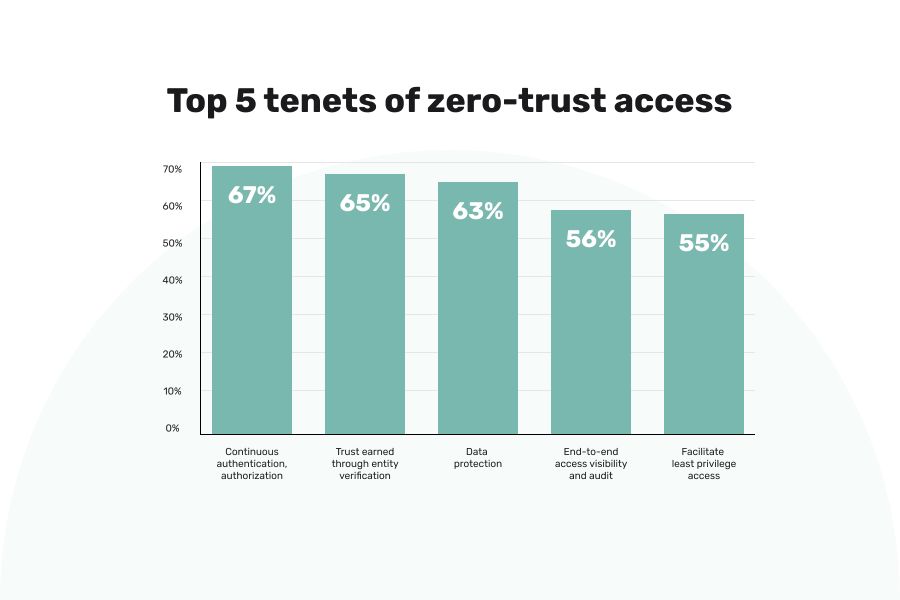
Finally, one of the most prominent ways Zero Trust security works is through analytics. Extensive data collection allows your security team to better optimize your security framework for the specific threats that your company faces.
By using information from data sources based on, for example, user credentials and endpoint data, you can constantly adapt your security framework to make it more effective.
Remember that Zero Trust is a mindset rather than one specific policy - by assuming that every network user is a potential threat, data and analytics become the main tools to counter these potential threats.
Best Practices for Implementing Zero Trust Security
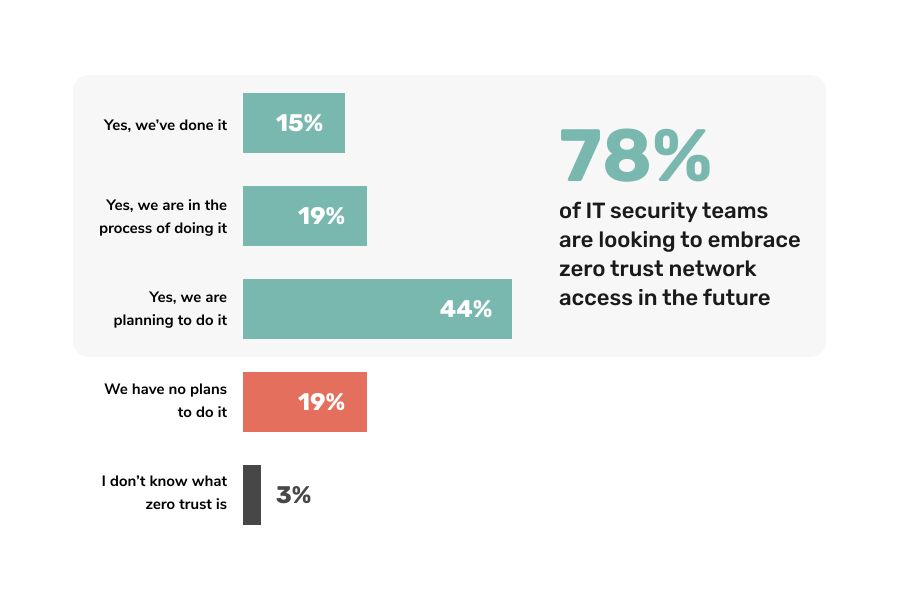
Now that you know what a Zero Trust security framework is and how it works, you will want to use it in your own online business. Going without a Zero Trust framework in this day and age will leave you open to insider threats. Follow these best practices to easily implement Zero Trust at your company.
1. Risk Assessment
You should begin your move to a Zero Trust security framework by assessing the specific risks that threaten your company.
Consider the sort of data stored on your network. If your company uses personal injury management software , for example, find out how much of this information is saved in your network. If personal information is stored unencrypted, this is a major risk that needs to be solved by encryption and least privilege access.
Also, look at how permissions are set up within your network. Remember that a Zero Trust approach sees all users as a potential threat, so permissions to access all files are an unnecessary risk that would have to be rectified later in the Zero Trust implementation process.
2. Divide and Encrypt Your Data
After assessing the specific risks to your network, you should begin to safeguard against those risks. One of the most important Zero Trust practices is micro-segmentation. This allows you to protect against internal threats and is a central step on the road to implementing least-privilege access across your network.
Micro-segmentation means that a user is able to access one part of your network doesn’t mean that they can access all parts of your network. In essence, each ‘micro’ section of your network is ‘segmented’ into smaller chunks, each with its security perimeter and verification requirements.
For instance, if an employee logs in to an IP phone system from home, micro-segmentation would mean that their potentially unsecured home network would not have access to any other parts of your network or data.
By using micro-segmentation in your network, alongside data encryption, any cyber threats that do enter your network will have a limited impact as they won’t be able to access the majority of your data. Limiting the range of attacks with micro-segmentation will save you money; on average, breaches cost $1,760,000 less at companies that used a Zero Trust approach.
3. Always Verify!
On top of micro-segmentation and encryption, consistent and repeated verification is one of the most important practices in a Zero Trust framework. As we highlighted earlier, Zero Trust assumes that every actor in a network is a threat until proven otherwise. Therefore, whenever a user wants to access a new part of the network or some new information, verification processes must be established.
This ensures that the micro-segmentation process is effective as access to one ‘segment’ of the network doesn’t mean that a user can access other ‘segments’. Meanwhile, use multi-factor authentication to ensure that verification is accurate.

However, you will also want to balance security with usability and productivity. If you run a small marketing or lead generation company, it shouldn’t feel like you are entering Fort Knox every time you access the network. Consider requiring verification once a week and only use it constantly for access to sensitive parts of the network.
The traditional model of one-time verification leaves your network open to vulnerabilities in the user’s technology and repeated verification guards against this.
4. Analysis and Moving Forward
Perhaps the most important Zero Trust practice that you can adopt is to remember that it is a mindset that needs to be constantly applied and updated across your network.
Once you have implemented the key parts of a Zero Trust framework - micro-segmentation, encryption, and verification - you should collect and analyze data from your network to examine its efficiency. Conduct a regular audit of your security systems such as an Auditboard security audit . Responding to this data to make your network more secure is an important part of a Zero Trust approach.
Security training is part of this to respond to weaknesses in the data and make your staff more aware of the need for a Zero Trust approach.
Zero Trust Security: The Future of Network Security
Zero Trust security frameworks are the way forward for all businesses and organizations that use a network or store data in the cloud, especially as more users access such networks from home.
By implementing a few key best practices, you can join the growing number of networks that are protected by a Zero Trust framework; micro-segmentation, encryption, and verification are all indispensable tools as you protect yourself against increasingly complex online threats.